I Am The Cavalry co-founder Josh Corman’s blog series “Building a Better Anonymous” was featured by Modern Diplomacy.
I Am The Cavalry's Beau Woods spoke about the rise of malware attacks threatening health care systems during the global pandemic in a CyberScoop article.
I Am The Cavalry co-founder Josh Corman provided expertise on the hacktivist organization, Anonymous, for a Dark Reading article regarding the group’s recent actions.
The Massachusetts Digital Health Initiative, a public-private partnership between the state of Massachusetts and several companies […]
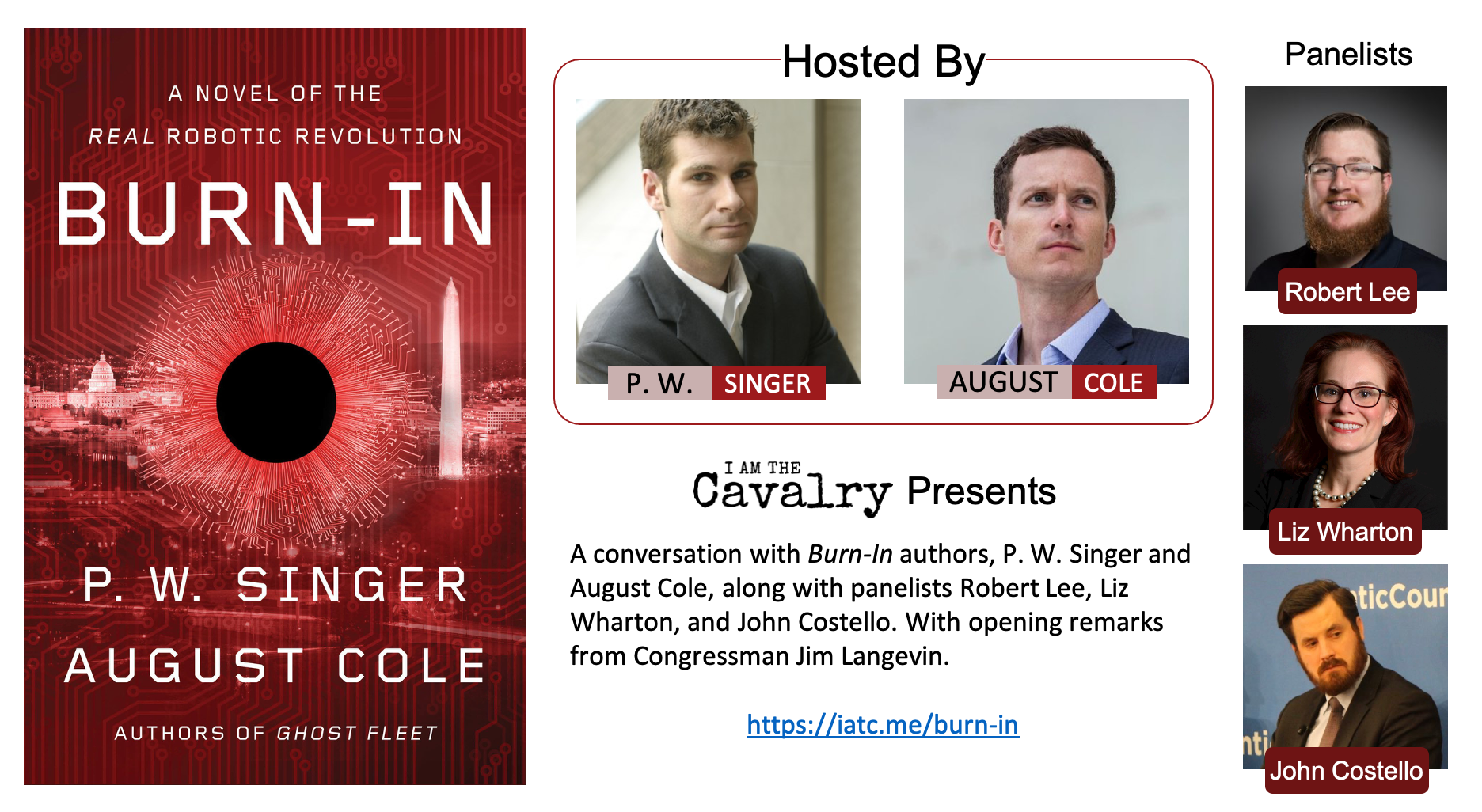
I Am The Cavalry brings together leaders in ICS security for a narrative-driven discussion about how IOT, Industrial IoT, and Public Infrastructure security decisions of 2020 will shape resiliency and vulnerability throughout the next decade.
I Am The Cavalry co-founder Josh Corman’s background knowledge on the organization, Anonymous, was quoted in a Forbes article on a reported leak regarding President Trump.
I Am The Cavalry co-founder Josh Corman’s writing about the organization, Anonymous, provided background in a Forbes article on the hacktivist collective’s actions against the Minneapolis Police Department in the wake of the death of George Floyd.
I Am The Cavalry's Beau Woods talked with POLITICO’s Morning Cybersecurity about some of the changes and adaptations being seen as a result of the upcoming DEF CON IoT Village event going virtual.
I Am The Cavalry's Beau Woods spoke with Stacey on IoT about UL’s IoT device security certification program.
I Am The Cavalry's Josh Corman and Beau Woods were both featured experts in an Atlantic Council article on ensuring security of the global IoT supply chain.